The Japanese Keyword Hack is a common issue across CMS platforms, especially WordPress. It injects malicious code that generates spammy pages filled with Japanese text and redirects visitors to scam or fraudulent websites.
This compromises your site’s security, damages your reputation, and can hurt SEO—sometimes even triggering Google penalties.
If you’re seeing strange Japanese titles in search results or unfamiliar pages on your site, it’s likely infected.
In this knowledgebase guide, we will show you how to identify, fix, and prevent the Japanese Keyword Hack from wreaking havoc on your WordPress site.
1 What is the Japanese Keyword Hack?
The Japanese Keyword Hack is an SEO spam attack where hackers exploit your website’s vulnerabilities, often targeting SEO-related features. By inserting hidden Japanese text, keywords, or spammy content into your site’s pages, posts, or metadata, they manipulate search engine rankings to their advantage.
This hack is sometimes referred to as “Japanese SEO spam” or “SEO poisoning.” It’s similar to the infamous pharma hack, where hackers use compromised sites to promote other websites—typically for illegal or unapproved products like counterfeit goods or grey-market items.
While this malicious content may not be immediately visible to your regular visitors, search engines can detect it. As a result, your site’s SEO performance suffers, your credibility takes a hit, and you risk penalties from search engines like Google.
2 Key Signs of the Japanese Keyword Hack
If you suspect your website might be compromised, especially with the Japanese Keyword Hack, there are several warning signs to look out for.
One major clue is the sudden appearance of new pages filled with autogenerated Japanese text. These pages often have unusual directory names and are loaded with affiliate links, directing users to questionable online stores. Worse, they might start showing up in Google Search results, tarnishing your website’s reputation.
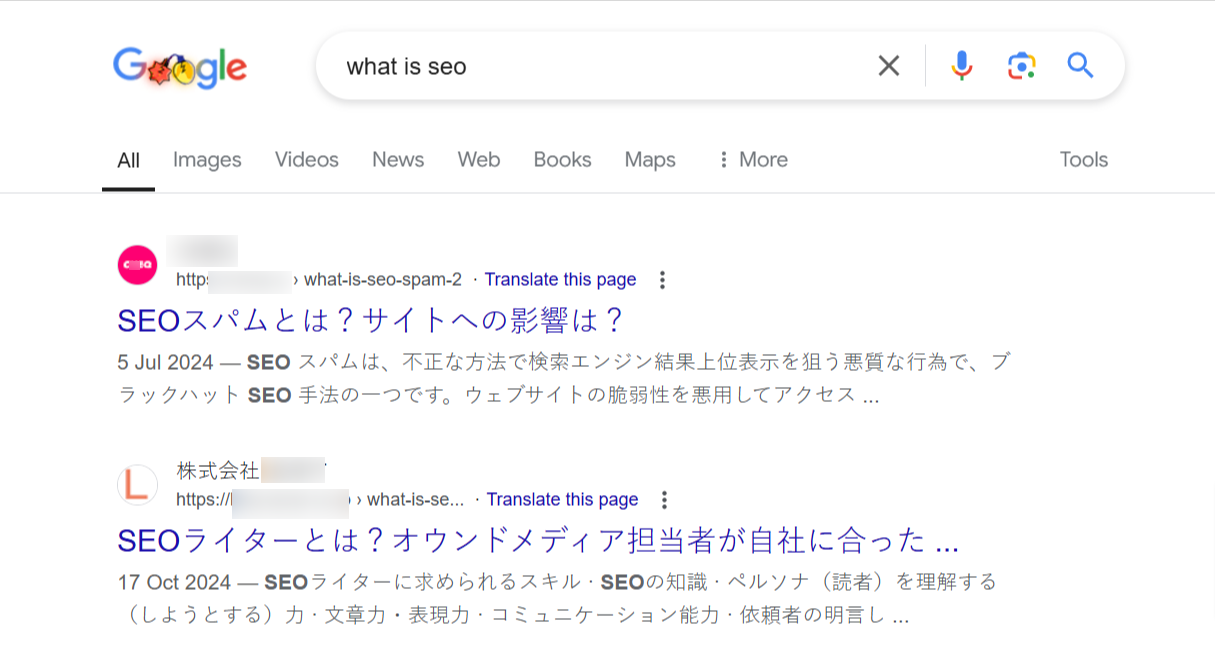
Another red flag is receiving notifications about unfamiliar users accessing your Google Search Console account. Hackers commonly add themselves as verified users, allowing them to manipulate crucial settings like geotargeting and sitemaps. It’s essential to periodically review your verified users in the Search Console and revoke access for any suspicious users.
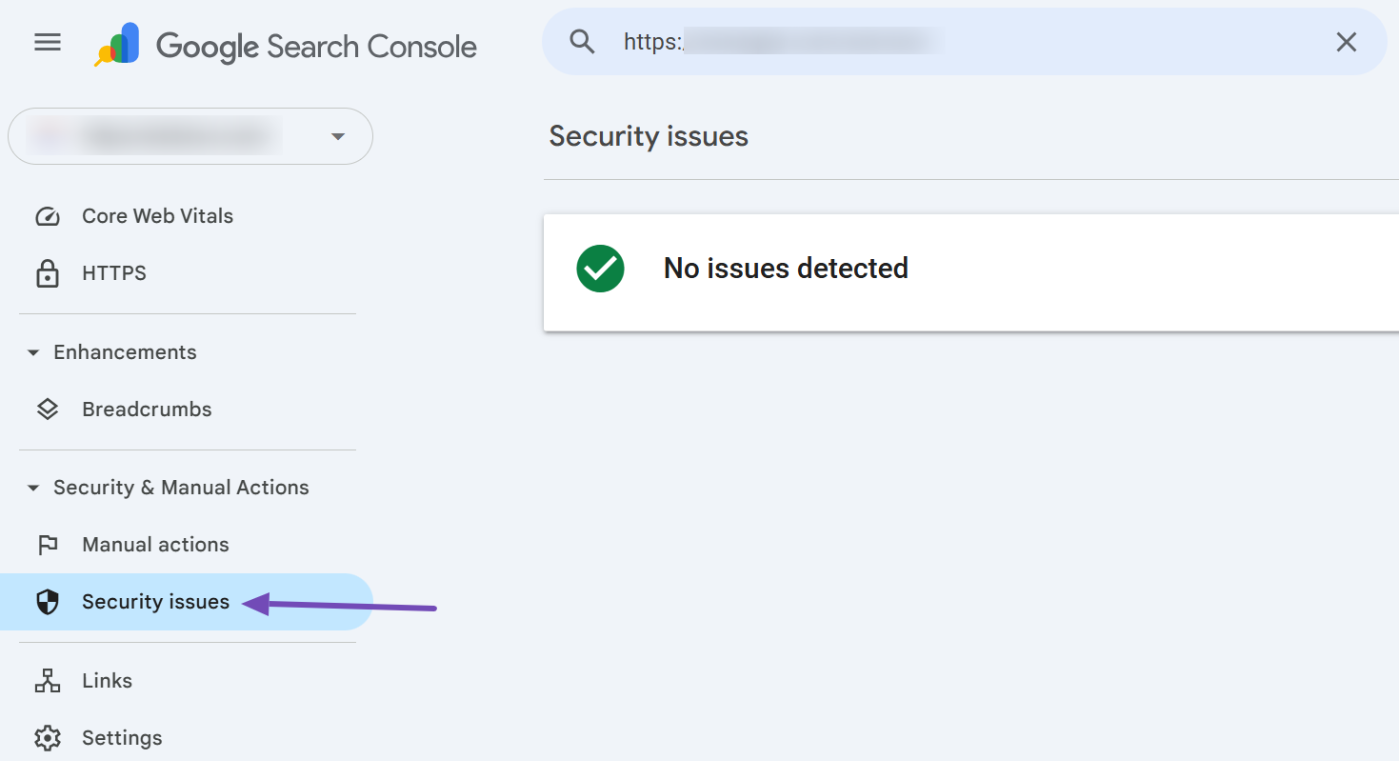
Don’t forget to check the Security Issues tool in Google Search Console (found under Security & Manual Actions → Security Issues). This tool can help you identify any hacked pages flagged by Google.
Other telltale signs include gibberish content or unexpected redirects when clicking links to compromised pages. Sometimes, hackers set up fake 404 errors to give you the false impression that the issue has been resolved.
To dig deeper, use the URL Inspection tool in the Search Console to check for cloaking. The Fetch as Google feature can reveal hidden content that regular users wouldn’t see.
Finally, perform a Google search using the query site:your-site-url to identify any suspicious indexed pages. If nothing turns up, try the same search on other search engines and carefully scan the results for unusual URLs. If you spot anything unusual, it’s time to act and secure your website.
3 Steps to Fix the Japanese Keyword Hack
Let’s walk through the steps to fix the Japanese Keyword Hack. Before starting, it’s crucial to completely back up your WordPress website—both files and databases. This precaution ensures you can restore your site in case anything goes wrong during the cleanup process.
3.1 Remove Newly Created Users from Google Search Console
Hackers often add themselves as users in your Google Search Console account to manipulate your site settings. If you notice unfamiliar accounts, it’s essential to revoke their access immediately. But how can you know if a new user has been added?
When your site is verified in the Search Console, Google sends an email notification whenever a user is added. To review your users:
- Log in to your Google Search Console account.
- Select the affected domain property.
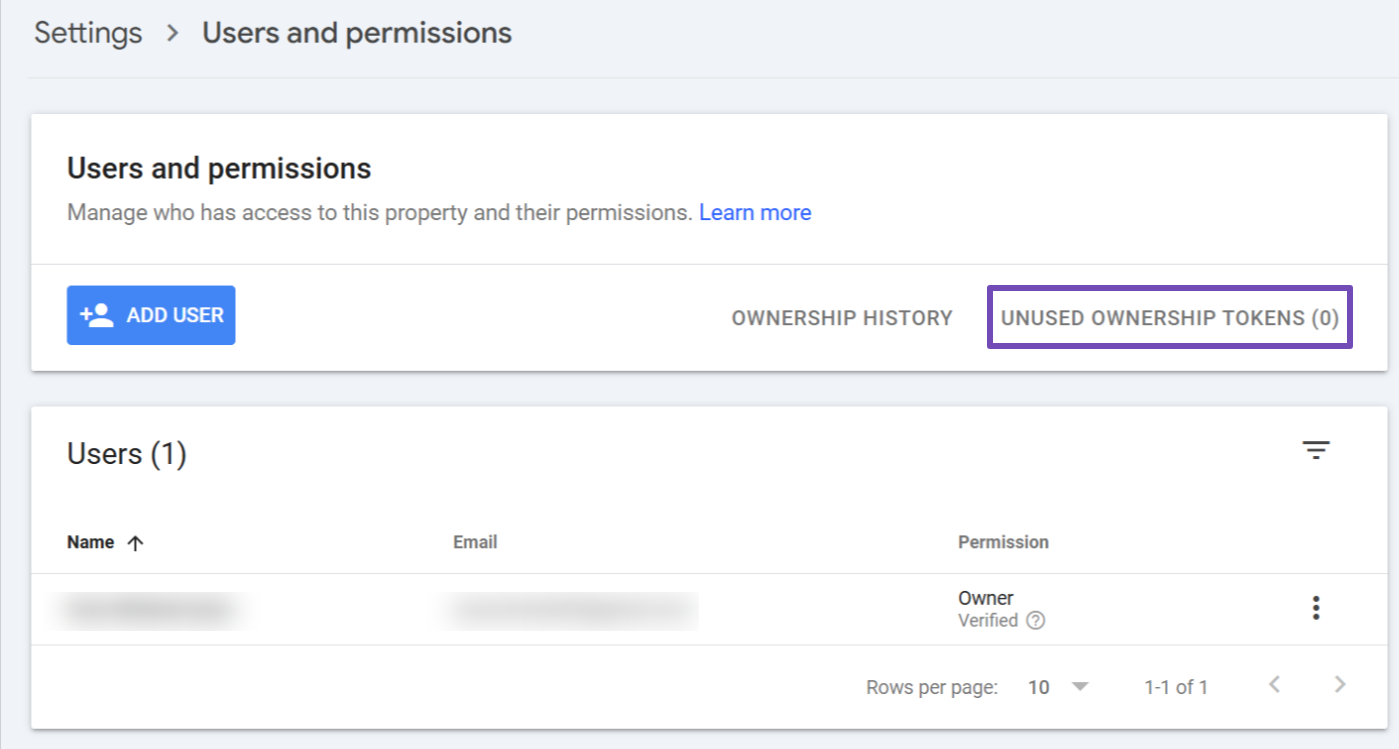
- Navigate to Settings, then choose Users and permissions, as highlighted below.
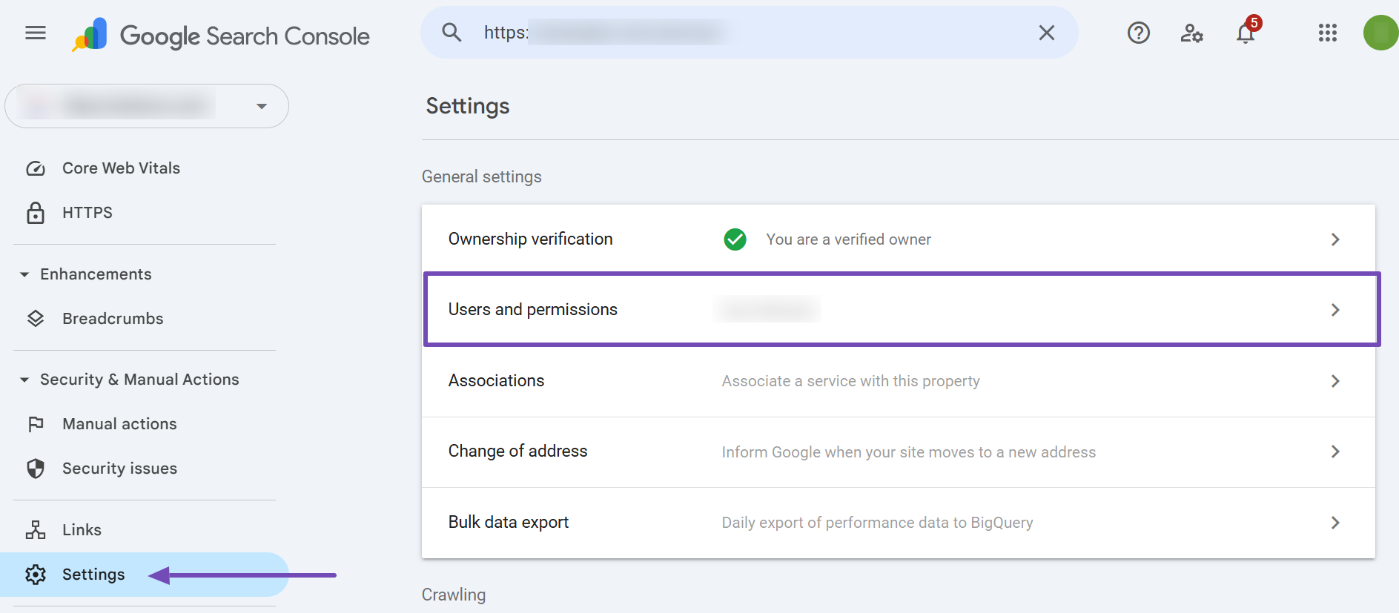
Here, you’ll see a list of all users and their permissions. If you identify an unauthorized user, click the three dots next to their permission status and select Ownership verification details. This option shows how the user verified their ownership.
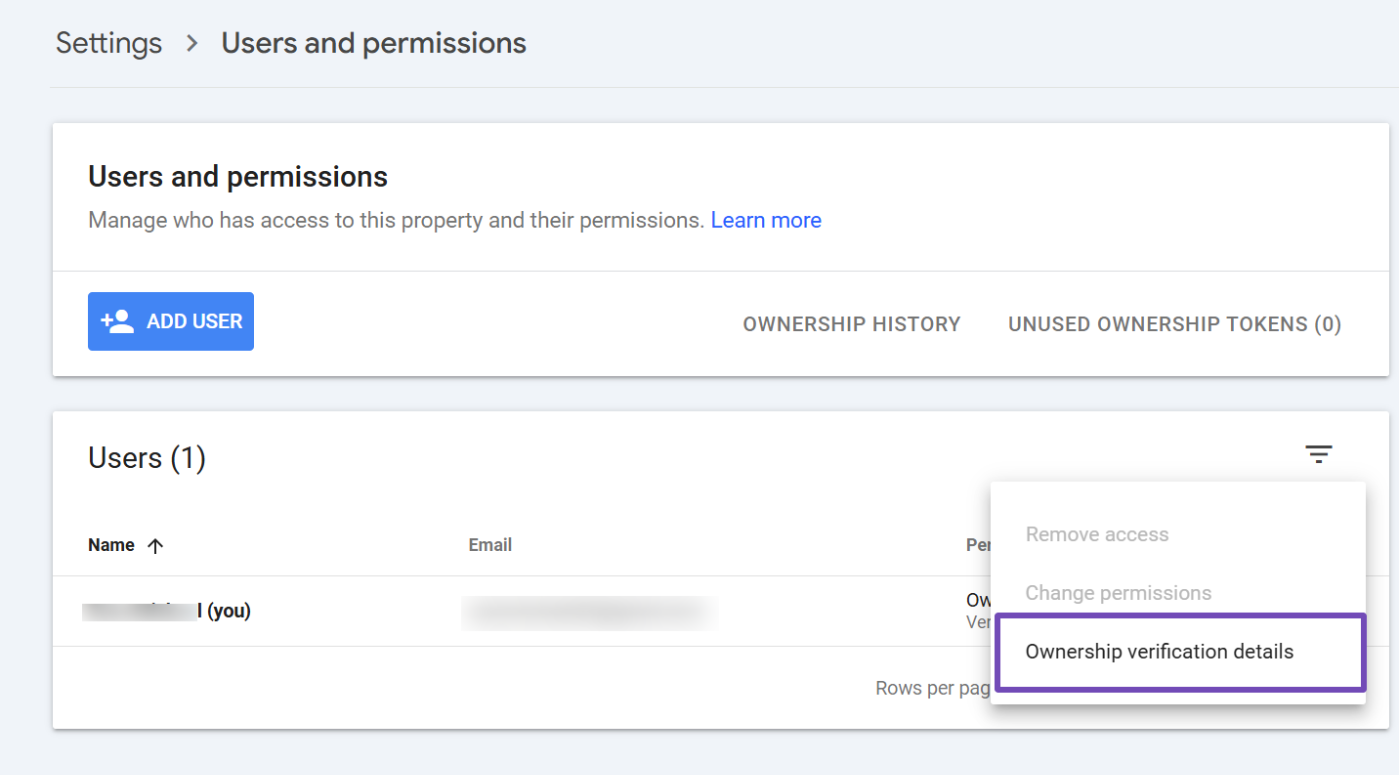
To remove the intruder, click the three dots again and choose Remove access.
If the user was verified before you revoked access, you must also remove the associated verification tokens. These tokens are methods used to establish ownership, and if left intact, the hacker could reverify ownership and regain access.
To remove ownership tokens:
- In the same Users and permissions section, find and select UNUSED OWNERSHIP TOKENS for the intruder.
- Then, follow Google’s guide to locate and delete any verification tokens embedded in your website (such as meta tags, HTML files, or DNS records).
3.2 Check and Restore .htaccess
If a hacker used an HTML verification token for property verification in your Search Console, they might have also implemented dynamic rewrite rules in your .htaccess file to mimic the HTML file verification.
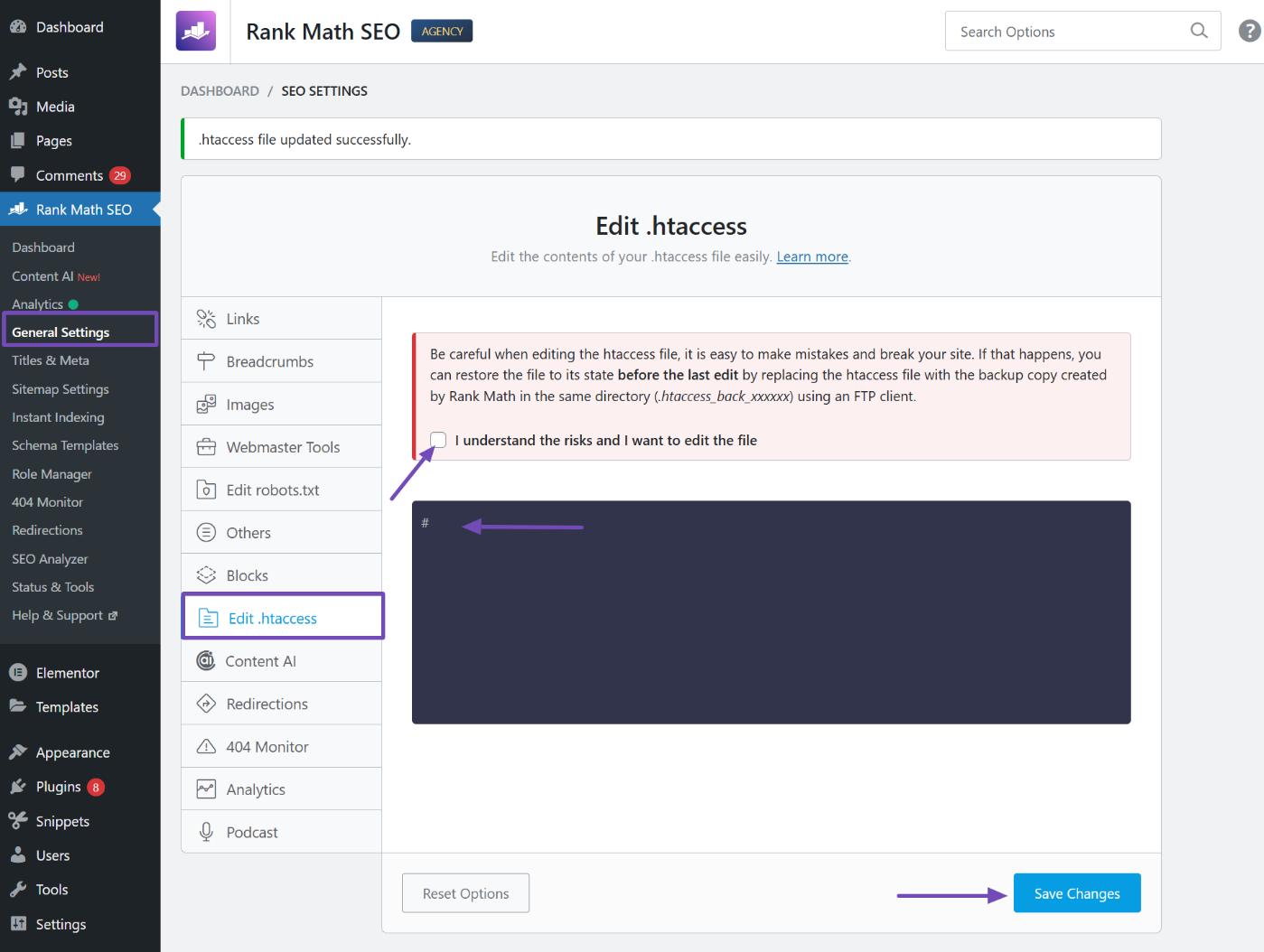
To address this, you’ll need to access your site’s .htaccess file and remove any suspicious rewrite rules. A straightforward way to achieve this is by utilizing the Rank Math SEO plugin. Once installed, set it up and navigate to Rank Math SEO → General Settings → Edit .htaccess from your WordPress admin.
Aside from dynamic verification tokens, hackers often use .htaccess rules to redirect users or create spammy gibberish pages. If you’re unsure about your .htaccess rules, replacing the file with a fresh version is a safe choice.
To do this, open the .htaccess file, highlight the entire code, and temporarily replace it with a single character like #. Then, click the Save Changes button to save.
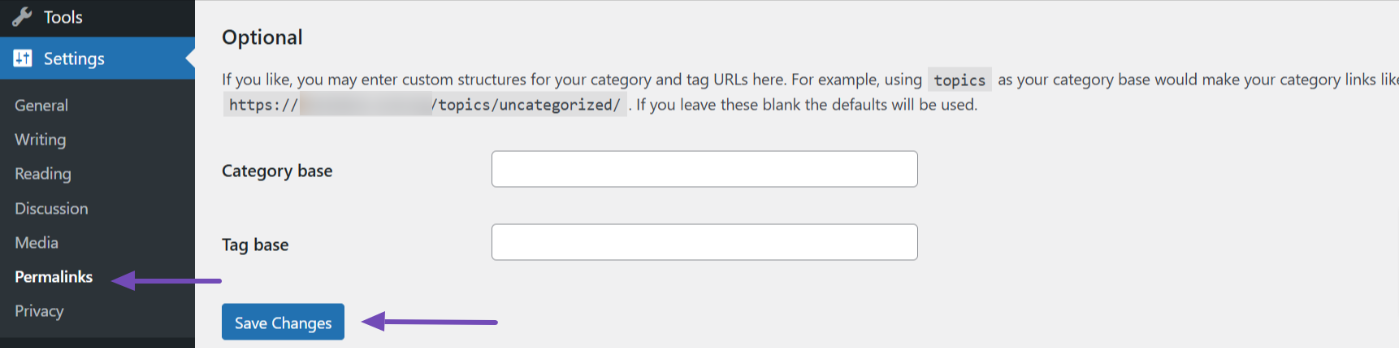
Then, go to Settings → Permalinks in your WordPress dashboard and click Save Changes without making any changes. This action will automatically regenerate your site’s default .htaccess file.
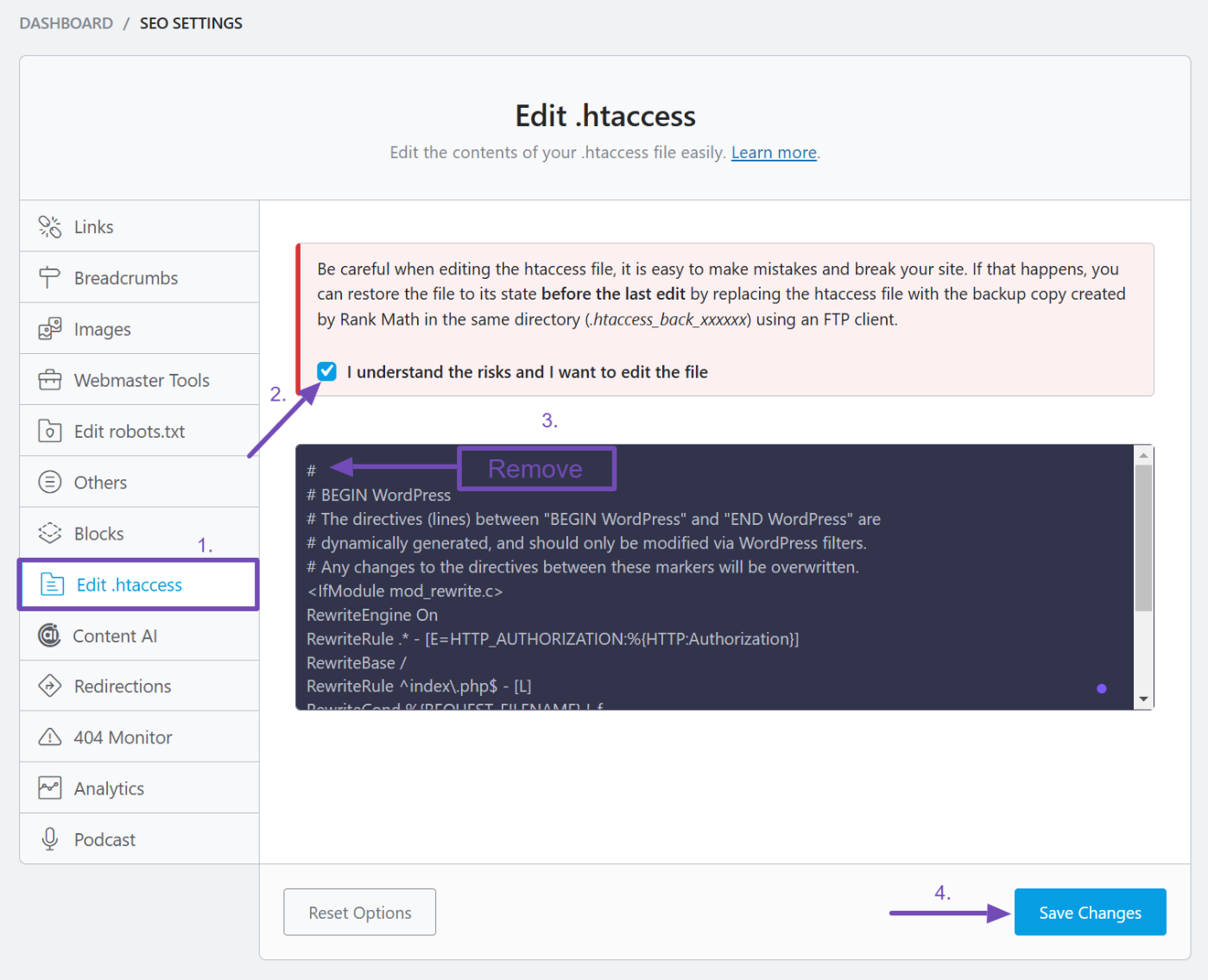
After that, return to the Rank Math .htaccess editor, remove the placeholder character (#) you added earlier, and save the file again.
3.3 Run a Malware Scan
It’s crucial to conduct a comprehensive scan of your website to detect any signs of compromise. To do this, install a reliable security plugin like Sucuri, Wordfence, or Malcare, which can scan your site for malware and vulnerabilities.
Many of these security plugins also come with firewall features that help filter malicious traffic, monitor for signs of compromise, and virtually patch known vulnerabilities. Be sure to activate the firewall to restrict access from suspicious IP ranges and harden your website.
If the scan finds any harmful code, replace or delete the affected files immediately. You should also scan your database to remove any spam posts or unwanted content and review your posts, pages, and comments in the admin dashboard to ensure everything is clean.
3.4 Clean Your Site Database
The database is a common target for the Japanese Keyword Hack, as hackers inject malicious entries into tables to spread spammy content and retain access. Cleaning your database is a crucial step to remove the hack completely. Here’s a quick overview of how to do it effectively:
- Open phpMyAdmin from your hosting control panel and select your WordPress database.
- Inspect the
wp_postsTable: Look for and delete posts or pages with spammy titles, especially those in Japanese or unrelated keywords. - Check the
wp_optionsTable: Remove any suspicious options with names likebase64_codeorencoded values. - Review the
wp_usersTable: Delete any unknown admin accounts to block hacker access. - Examine Metadata: Remove unusual entries in
wp_postmetaandwp_commentmeta, such as_seo_metaor redirect links.
You can also use SQL commands to quickly identify and delete malicious entries, ensuring your database is free from hidden hacks.
3.5 Update and Reinstall WordPress Core Files
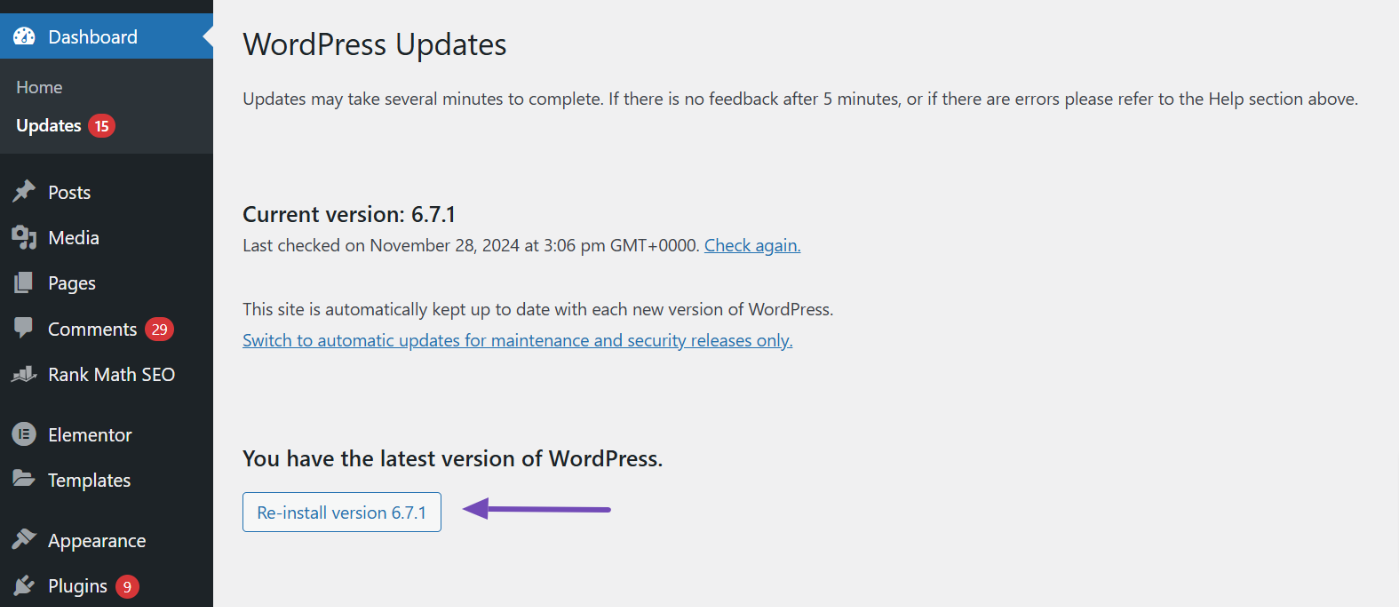
Hackers often modify WordPress core files, themes, and plugins to inject malicious code. To ensure your site is clean, start by updating WordPress to the latest version via the Dashboard → Updates section.
If your installation is already up-to-date, use the Re-install version button to refresh the core files with clean versions directly from WordPress.org.
For active themes and plugins, delete and reinstall fresh versions from trusted sources (e.g., from the WordPress.org repository). Avoid using nulled or outdated themes and plugins, as they are common hacking targets.
Remove any plugins or themes you no longer use to reduce vulnerabilities. This process ensures that all critical files are free from malicious modifications and helps secure your website.
3.6 Check and Clean WordPress Files
Hackers often insert malicious code into WordPress files, so it’s crucial to check and clean your installation regularly. Access your WordPress site through your hosting file manager or an FTP client.
Compare your core WordPress files (like wp-config.php, wp-load.php, wp-admin, and wp-includes) with fresh versions from WordPress.org. If any files appear modified or suspicious, replace them with clean copies.
Next, examine the wp-content folder, especially the themes, plugins, and uploads directories. Look for unusual files, such as PHP scripts in the uploads folder or files with strange names like tmp.php, bkp.php, .js, or .ico, or random strings (e.g., base64_decode, eval, str_rot13, gzinflate, etc.). Also, check for scripts in unexpected locations, like wp-content/cache or wp-content/tmp. If you find any, delete them.
By cleaning these files, you’ll remove malicious code and strengthen your site’s security. For files you’re unsure about, use your security plugin to verify their integrity.
Note: Attackers commonly inject scripts into the following files: index.php, wp-load.php, 404.php, and view.php. It’s crucial to check these files regularly for any unauthorized changes.
3.7 Check Sitemaps for Suspicious Links
Sitemaps are important for search engines to index your site, but hackers can also exploit them to spread malicious links. After a hack, attackers may add suspicious URLs to your sitemap to drive traffic to harmful sites.
To check for suspicious links, open your sitemap (usually found at example.com/sitemap.xml or example.com/sitemap_index.xml) and carefully examine the listed URLs. Look for any unfamiliar or unrelated links, such as those pointing to suspicious websites or containing random characters.
If you find any suspicious links, remove them from your sitemap. You may also want to regenerate the sitemap using the Rank Math SEO plugin to ensure it’s up-to-date and clean.
After cleaning your sitemap, resubmit it to search engines like Google and Bing via their webmaster tools to ensure they crawl only legitimate, safe links.
3.8 Reset All Passwords
After a security breach, it’s essential to reset all passwords associated with your WordPress site to prevent unauthorized access. Start by changing the passwords for your WordPress admin accounts.
Then, update the credentials for your hosting control panel and FTP accounts, as these can be exploited if compromised. Don’t forget to reset the database user password as well to ensure no backdoor access remains.
Use strong, unique passwords for all accounts, and consider using a password manager to securely store them. By resetting all passwords, you’ll significantly reduce the risk of further attacks.
4 What to Do After Resolving the Hack
Once you’ve resolved the Japanese keyword hack, there are a few essential steps to take to restore your site’s security and SEO health. If Google flagged your site for malicious activity, submit a reconsideration request via Google Search Console Security Issues report to inform them that the issue has been resolved.
Next, work on restoring lost SEO rankings. Use the Rank Math SEO plugin to rebuild your SEO settings. Check for any affected metadata, sitemaps, or canonical tags and update them to ensure everything aligns with best practices. Finally, resubmit your XML sitemap to Google Search Console so search engines can reindex your site and recover any lost traffic.
By taking these steps, you’ll help get your site back on track and secure its position in search results.
5 Best Practices to Prevent Future Japanese Keyword Hacks
To protect your site from future Japanese keyword hacks and other security threats, it’s essential to implement proactive security measures. Here are some best practices to strengthen your WordPress website:
- Regularly Update WordPress and Plugins: Ensure that you keep WordPress, your themes, and plugins up to date. Regular updates patch known vulnerabilities and reduce the chances of a hack.
- Use Strong, Unique Passwords: Use complex passwords for all your accounts (admin, FTP, hosting, etc.), and avoid reusing them across multiple sites. Consider using a password manager to securely store them.
- Enable Two-Factor Authentication (2FA): Implement two-factor authentication for your WordPress admin area and any other sensitive logins to add an extra layer of security.
- Install a Web Application Firewall (WAF): Utilize a firewall, such as those offered by Wordfence, Sucuri, or iThemes Security, to filter out malicious traffic and block harmful requests before they reach your site.
- Limit Login Attempts: Use plugins to limit login attempts and prevent brute-force attacks. This will protect your site from automated login attempts that often precede a hack.
- Regular Backups: Set up automatic backups to ensure you can quickly restore your site in case of an emergency. Store backups in a secure location outside of your hosting environment.
- Secure File Permissions: Set correct file permissions for WordPress files and directories to limit unauthorized access. Avoid giving write permissions to sensitive files unless absolutely necessary.
- Monitor Your Site’s Activity: Regularly monitor your website for unusual activity, such as sudden spikes in traffic or unknown file changes. Use a security plugin to help with real-time monitoring. Additionally, use them to scan your website regularly.
- Remove Unused Themes and Plugins: Regularly audit your themes and plugins, removing any that are no longer in use. This reduces your site’s attack surface and minimizes vulnerabilities.
- Review User Permissions: Limit user access to only what’s necessary. Regularly review user roles and remove access for users who no longer need it.
Following these steps will help restore your site’s security after a Japanese keyword hack. If the hack persists or you’re unsure about handling WordPress files or databases, seek professional help from security services or a WordPress security expert.
And that’s it. We hope you’ve learned about the Japanese Keyword hack and how to fix it. If you have any further queries or need assistance with Rank Math, you are more than welcome to reach out to our support team. They’ll be happy and willing to assist you.